30+ firewall configuration diagram
Its free to sign up and bid on jobs. Username admin privilege 15 secret Strongpasshere.
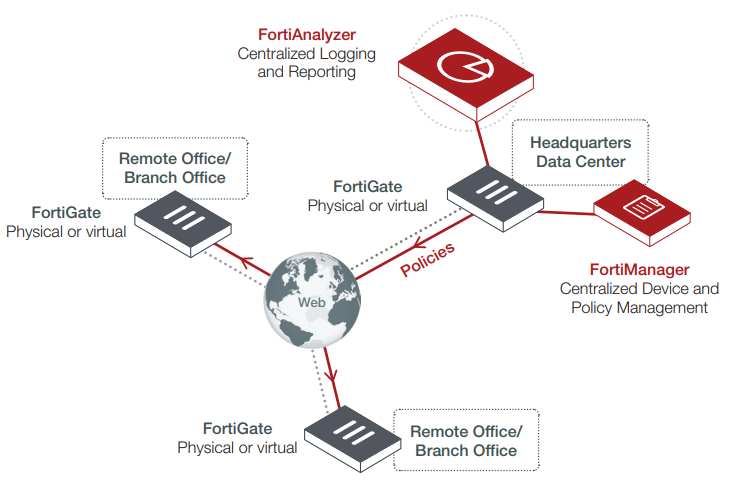
Fortinet Fortianalyzer 200f Avfirewalls Com
A network administrator may want to define polices so that only traffic from VLAN 30 at Site A is.
. Security Level Configuration Tool. A hardware firewall is a physical device that attaches between a computer network and a gateway. The basic firewall network diagram template demonstrates how firewalls can be integrated into a network.
Security Management R8030 Administration Guide - Check Point Software. For example a broadband router. To simplify the configuration process the firewall policies can be created at a Global level.
Screened subnet firewall configuration. It has a built-in Ethernet card and hub. This is an example of a network diagram illustrating how firewalls may be integrated into a network.
Before you install the server you must ensure that servers agents and other systems can connect to each other through your networks and. The below Network Diagram uses Visio-like Network Diagram. FPGA-to-HPS AXI Slave Interface 304.
On the other hand a software firewall is a simple. With a hardware firewall the firewall unit itself is normally the gateway. Here are a number of highest rated Firewall Configuration Diagram pictures upon internet.
Firewall and communication configuration. Access management and logging configuration. Create network designs like this using SmartDraws extensive library of network.
Arria 10 SoC FPGA Configuration Sequence Through FPGA. A good example is the Linksys CableDSL router. Clock and Reset Interfaces 303.
I think that the diagram should be updated to a new one where the user contributor role can ignore firewall rule settings. In this lesson Im going to discuss firewalls and the configuration of different kinds of firewalls. In a front-end back-end ISA firewall configuration you may not wish to make the ISA firewall a member of a domainIn that case you can use RADIUS authentication for remote access VPN.
Search for jobs related to Firewall configuration diagram or hire on the worlds largest freelancing marketplace with 20m jobs. DATABASE-LEVEL FIREWALL RULES Client IP Address in Range. During the Firewall Configuration screen of the Red Hat Enterprise Linux installation you were given the option to enable a basic firewall as well as to.
When establishing a firewall you should follow the best practice of least privileges which implies banning anything that isnt used for a specified and allowed business function. We identified it from reliable source. In this configuration two packet filtering routers are used one between the basiton host and internet and one between the basiton host and the.
So by end of the lesson youll able to tell me the differences between the types of firewalls and. Its submitted by government in the best field.
Should The Hardware Firewall Be Placed Before Or After The Router Quora

Cisco Network Diagram Network Organization Chart Computer Network Cisco Networking Networking

8 Ways To Detect Malicious Firewall Traffic Using Siem Blue Team Blog

Log Analytics Gateway Microsoft Tech Community

8 Effective Home Network Setup Diagram For Your House In 2022 Smart Network Geek
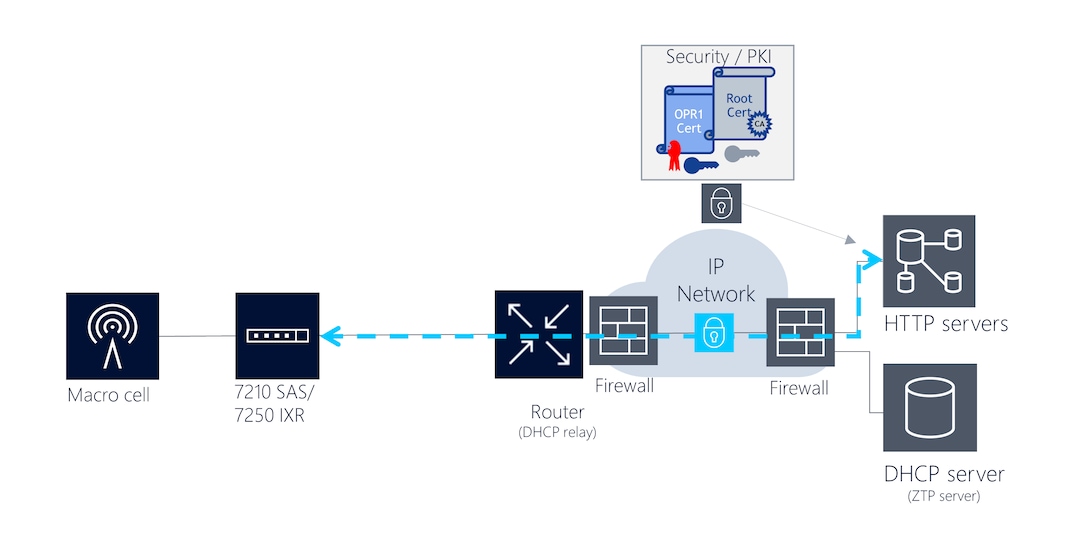
Simplify Mobile Transport Network Rollouts Nokia

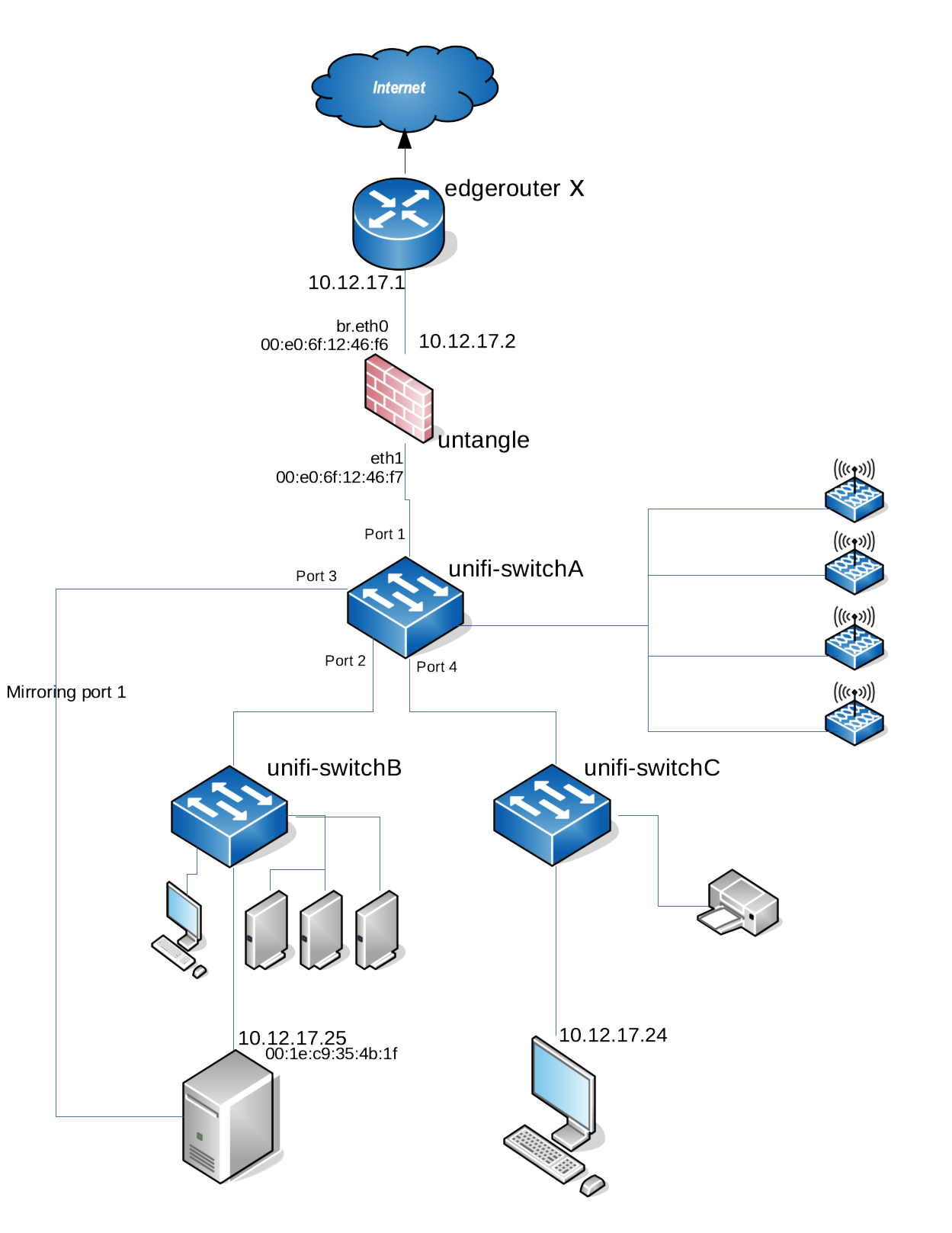
Errant Frames Going To Wrong Port Was Duplicate Icmp Packets Ubiquiti Community

8 Effective Home Network Setup Diagram For Your House In 2022 Smart Network Geek
What Are The Three Questions That Must Be Addressed When Selecting A Firewall For A Specific Organization Quora
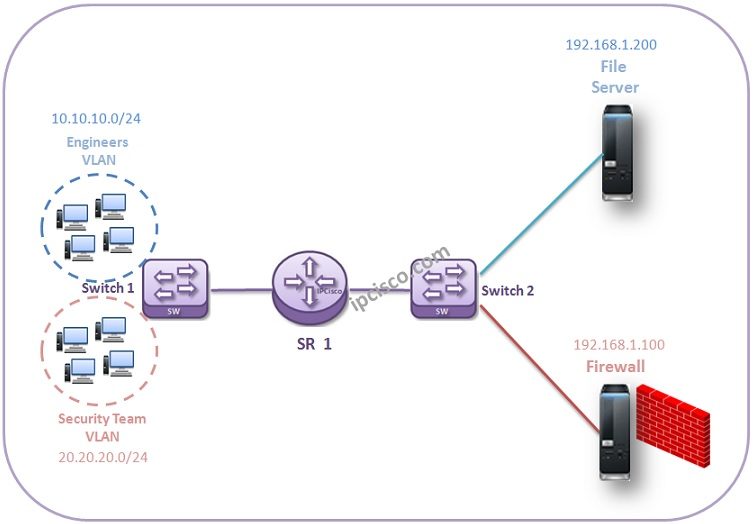
2 Ip Filter Examples Nokia Ip Filter Configuration Example 2 Ipcisco
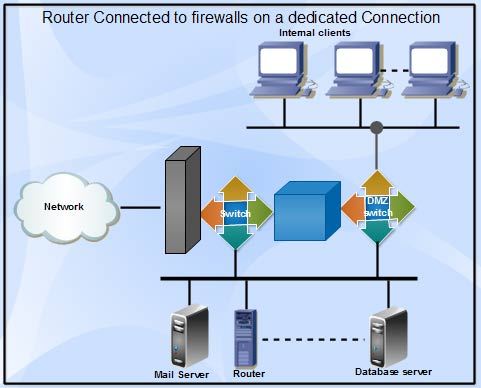
Firewall Explain Types Of Firewall Architectures Computer Notes

Cisco Asa Vs Next Gen Firewalls Ngfw Which One To Choose Youtube

Vyos On Aws Vyos

U02a1 Project Selection Networking Basics Computer Network Computer Technology

8 Effective Home Network Setup Diagram For Your House In 2022 Smart Network Geek

Network Security Memo Info Security Memo
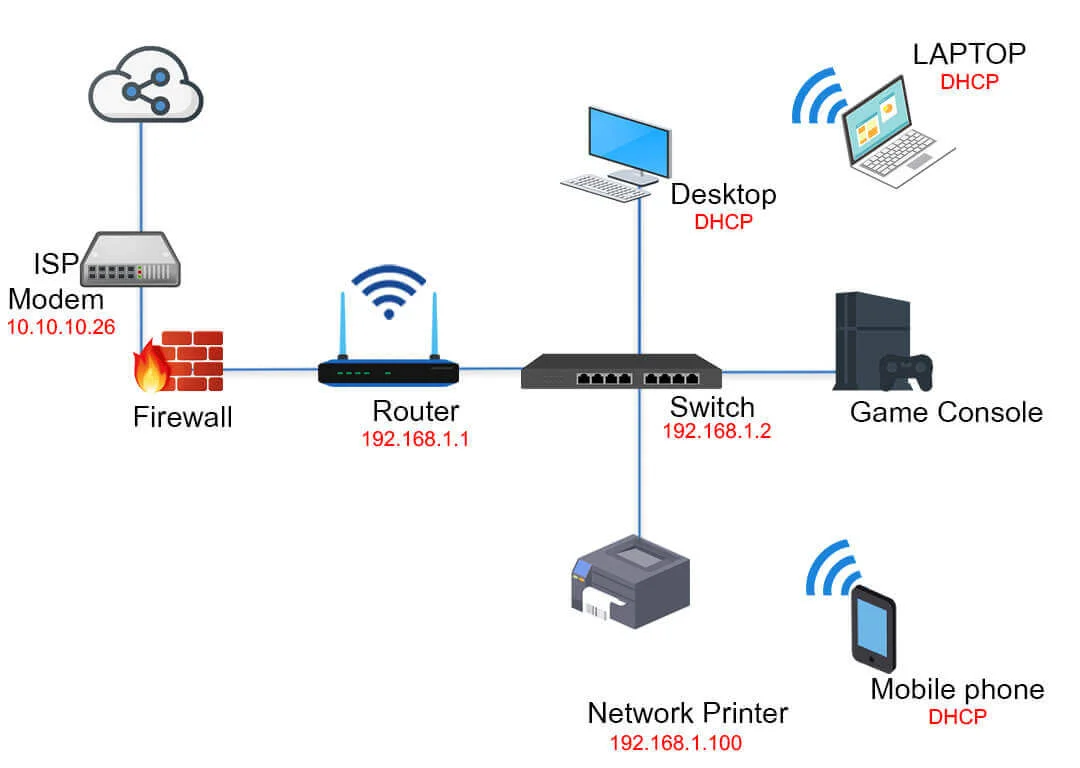
8 Effective Home Network Setup Diagram For Your House In 2022 Smart Network Geek